Jano is our server specialist, or, as we call him, a server guru. He makes sure that the machines on which our clients’ projects run, work like clockwork. What does Jano’s work day look like and what does he like to do in his free time?

Jano, what does the work on the position of a “server guru” involve?
In the company, I take care of server infrastructure – installation, configuration, updating, optimization of their performance and adaptation to requirements. This server infrastructure consists of a computer network, disk arrays and servers. Within the computer network, I take care of the design of its division (public, private, VPN), assignment of IP addresses, routing settings, DNS and the like.
My job includes monitoring the network as well. This is done through the Nagios program, which usually reports problems to us before the customer notices, but also through our own TrafGrapher tool – it helps visualize the performance of servers and in case of a problem, determine how it happened.
I focus mainly on opensource technologies, i.e. mainly Linux and
the applications in it. For work I still use mainly a text terminal and a web browser firefox, using which I do almost all my work. As a developer of the Fedora Linux distribution, I contribute as a tester and an application package manager with the “proven packager” level.
What does “proven packager” mean?
The packager status is obtained by a developer after demonstrating their ability to create installation packages for OS Fedora or EPEL. Normally, they only have access to their packages, or to others where someone has given them access. However, a proven packager has access to most packages, almost the entire system, and can fix bugs in them when the conditions are met.
So not only do you care about security in our company, but you protect developer projects all around the world through the status of a proven packager. We’re very happy to have such a person in our company. What does your workday look like?
It starts by checking e-mails. Every day, the servers write me an “essay” about how they were doing the previous day. What they did, what pitfalls they had to face (e.g. hacker attacks) and what’s new.
What’s new?
Updates ?. In some cases attacks or other server problems. The next steps depend on what I’ve learned in these reports. If I find a problem there, depending on the severity, I solve it immediately or plan to fix it later. I try to respond to simple things immediately so as not to impede anyone.
And we thank you for that ?. Are there situations where you have to resist hackers?
Absolutely. But maybe it’s not as often as people think. The question is, what do they think of as a hacker? Most often it’s some virus or script that tries to exploit security holes in the system.
And the smartest way is to prevent the attacks, right?
Yes, I’m trying to prevent attacks by properly securing the systems. This mainly includes regular updates to have all security holes patched, but also security by restricting access, e.g. through a firewall. Another problem is DOS or DDOS attacks, when an attacker tries to overload and thus shut down our services.
Why do hackers need to attack a website? What do you think they get from it?
In our case, their main motive is to exploit the performance of our servers for further attacks and spamming. With further attacks, they acquire more and more additional resources, connect additional servers to their infrastructure, and thus increase their performance. I also encounter the fact that they mine cryptocurrencies on servers. Sometimes they may want to obtain sensitive data (personal data, passwords, etc.).
Can hackers attack private individuals as well? What should we be careful about?
They sure can. With different viruses, for example. But those must have been written by an attacker. Phishing also causes a lot of problems, when an attacker tries to obtain users’ access passwords based on false claims.
Each user should properly secure their devices, update software, set up a firewall, install antivirus. However, the behaviour of users is also important – not to download software from an unverified source on the Internet and to be careful where they enter their personal data.
We know that even a server needs to be turned off sometimes so that it can rest. How do you turn off?
I like cycling and hiking. Thanks to my colleague, I discovered geocaching at a time when I didn’t have a cell phone with GPS. And today we sometimes go on a trip because of geocaching, and sometimes we “just” go hiking and forget about geocaching ?. I also like to make things out of smart components like Arduino. I was at an open source presentation where they talked about this platform. It’s the most famous platform – reasonable price and good support.
And what have you made on Arduino lately?
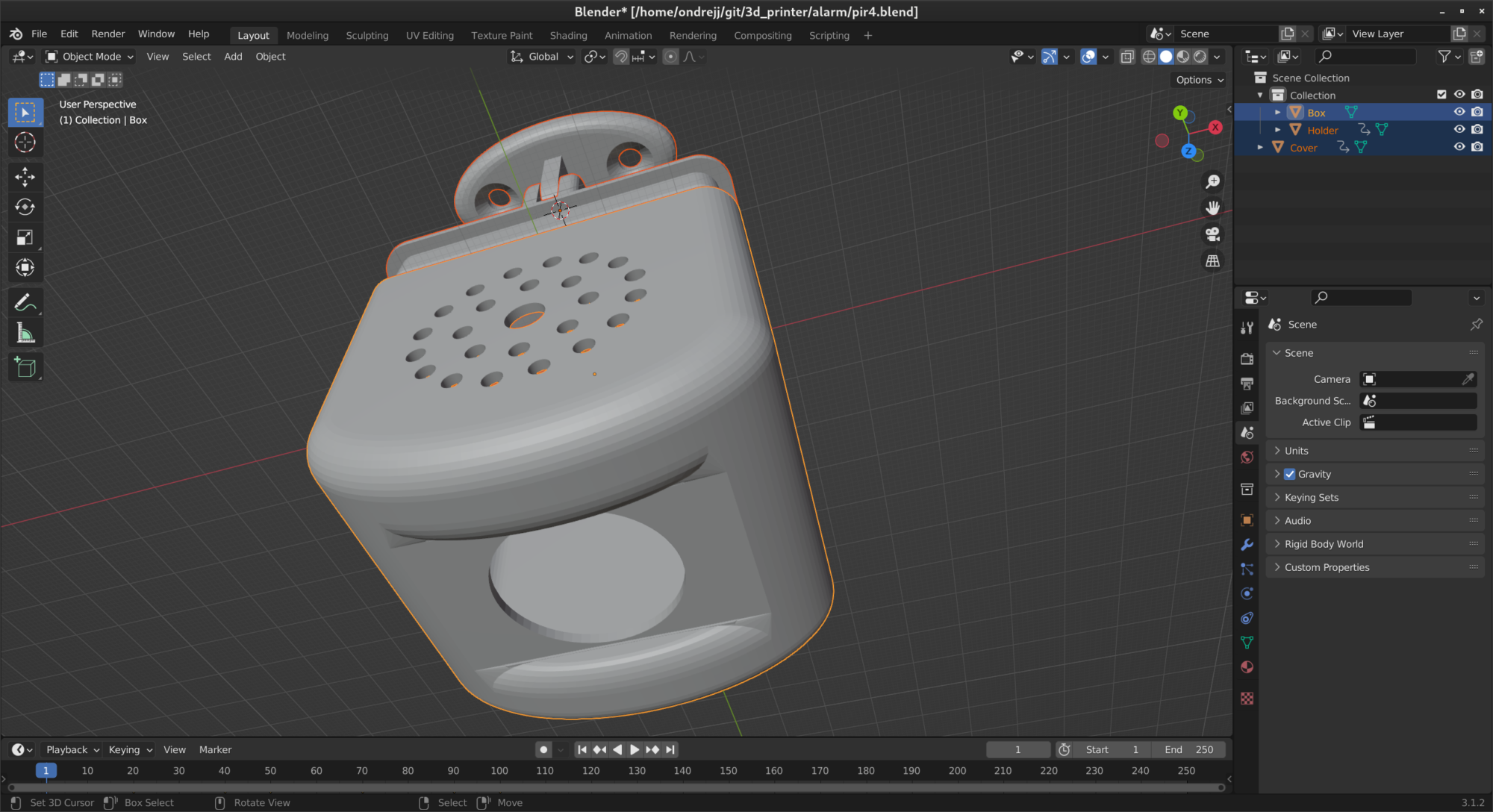
Most of them are small household items and a monitoring system – an alarm and sensors. But I also bought a 3D printer, learned how to work with it and design my own models. Most recently, I made a box for the alarm.
We can see that safety is not only your work, but also your life. This topic is very broad and we’ll focus on it – next time at the Frontend Masters event, in the preparation of which you participated as a specialist consultant. For that, as well as for the interview, we thank you, and we invite the rest of you to the Aston Building on June 7th at 18:00 – live again after a long time!