War conflicts of modern history are no longer just about heavy fighting on the frontlines. The fight is also transferred to cyberspace, where stakeholders can gain a considerable advantage by decommissioning important infrastructure. We are also currently witnessing a conflict where there are attempts to disrupt systems in various sectors. One of the methods of an attack that we can observe is DDoS.

What is a DDoS attack?
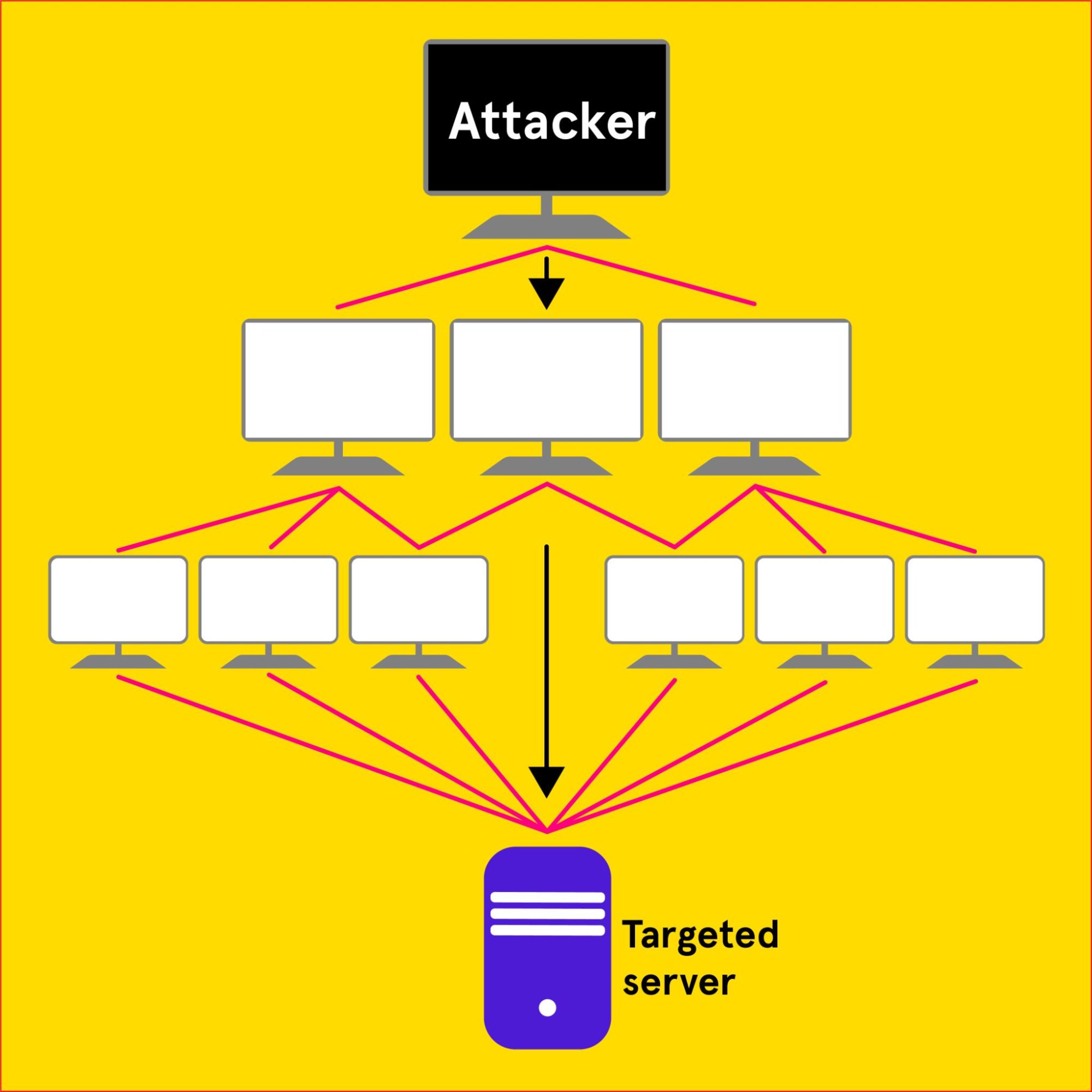
DDoS or Distributed Denial of Service is an abbreviation composed of two terms – “denial of service” and “distributed”, meaning based on a larger number of users.
The aim of the attack is to disable the server with an extreme amount of queries until the server is not able to process these queries. So it’s nothing more than a system overload. This attack could be compared, for example, to a strike of farmers, where the aim was to overwhelm important transport hubs with large volumes of machinery. These communication nodes were simply not adapted to such a heavy load and congestions occured. We are not talking about illegal activity, but only about the situation when everyone wants to go through the same section at the same time.

The same is true of the DDoS attacks. However, it doesn’t necessarily have to be an illegal activity when a large number of people want to browse the site at one point, for example. It may have characteristics of a DDoS attack, but it may not be so in the end.
Of course, when we talk about the DDoS attack in its true essence, it’s a sophisticated system to achieve this attack and unsuspecting users can often get among the attackers. For example, as my colleague Juraj mentioned in his article, everyone could “contribute” to making both Russian and Slovak websites malfunction.
The attack cannot gain any access or steal data. This is purely a disruption of the system.
DDoS attacks currently
Ukrainian people have also succeeded in several DDoS attacks. They managed to disable the website of the Russian state intelligence service RT News. Several attacks on Russian government websites have also been noted. As a defense against DDoS attacks, the government used a measure known as geofencing to block access to the pages it controls. One of these domains is, for example, the primary domain of the Russian army mil.ru. This site is currently blocked for visitors outside of Russia. Those who try to get on the web will get HTTP error 418. Interestingly, this bug code began to be used by Google in the 1990s as a joke “418 – I’m a Teapot”.
Global nature of attacks
The management of the Polish railways recently reported on problems in several local dispatching offices responsible for railway traffic management. They’re investigating the possibility of a hacker attack. In relation to this, they expect long-distance and regional trains to be delayed for several hours.
The Polish Minister of Infrastructure Andrzej Adamczyk said that the problem is “global in character” and doesn’t only concern Poland. He assured that train traffic would return to normal, but it was clear that some of the trains wouldn’t make it into traffic on the day of the attack.
The media have reported allegations that Russia is behind the as yet unconfirmed computer attack. According to them, for many years the Kremlin had been training the entire staff of people whose task is to destabilize other countries also in the field of critical infrastructure. United States has also been exposed to such attacks quite recently, the website Bezprawnik.pl reminded. According to them, “Poland is now becoming a target in connection with the Russian invasion of Ukraine”. (Source: TASR and SME.sk)

Attack Classification
Attacks can be divided by layer into attacks at the infrastructure level and on the application layer.
Attack on infrastructure layer
Attacks at levels 3 and 4. (OSI) layers are the most common type of attacks. These are user datagram packet (UDP) floods. These attacks are typically large in volume and aim to overload the capacity of the network or application servers. Fortunately, these are the types of attacks that have clear signatures and are easier to detect.
Attack on application layer
Although these attacks are less frequent, they tend to be more sophisticated. Application layer attacks are typically small in volume compared to infrastructure layer attacks, targeting specific parts of the application, making them inaccessible to users. For example, a flood of HTTP requests for a login page or an expensive search API.

How to defend yourself?
Minimize attack area
One of the basic techniques to mitigate and prevent DDoS attacks is to minimize the area that can be attacked. The attacker will be restricted in the location of the attacks. In practice, this means, for example, closing ports where we don’t expect any communication – we “brick” the entrance doors that are not necessary.
Identify what is and what isn’t normal traffic
It’s essential that we are only able to receive as much traffic as our server can handle and service without affecting availability. At the same time, the system should automatically be able to monitor the accessibility of the site and notify the administrator in a timely manner in the event of a significant slowdown or a complete outage.
Use Firewall
Firewall is one of the best defenses against DDoS attacks. It filters network traffic to prevent harmful access.
SYN Cookies
Internally, it modifies the behavior of the TCP protocol so that the server’s own resources are accessed only after the validation of the address. Implementation of this defense is common on Linux systems.