Alphabet Inc. (Google) recently uncovered Russian hackers who were involved in espionage, phishing campaigns and other attacks targeting, among others, Ukraine and its European allies.
Phishing affects all of us. You can read in a few minutes about how not to become its victim in our next article from the Online Safety series.

What is phishing?
It’s a type of attack where we want to obtain access details from the victim by planting a fake website. Phishingcan take many forms. For example, we may receive an email from a “bank” that provides us with some information and prompts us to log in. However, after opening the URL, we get to the attacker’s page and not the bank’s. The page’s design looks identical and so it isn’t easy to distinguish it at first glance.
Attack via Messenger and Text message
Another way can be an attack via Facebook Messenger or via a text message. Recently, we have registered several similar attacks in Slovakia. Specifically, it was a purchase of goods via bazos.sk. An attacker sent a link to a buyer to enter payment card details and the money would be automatically transferred. Of course, the page was fake – it stored the card details, which gave the attacker control over withdrawing money from the card.
How to protect yourself against phishing?
Whenever we receive an e-mail (or other kind of message) with a URL, we need to be vigilant. Even if it’s an email from a bank / trusted friend / family, we must assume that it was sent by an attacker in order to retrieve our data.
The safest way to verify it is not to click on the link, but to open the URL separately by typing it into your browser. For example, if you receive an e-mail from Slovenská sporiteľňa with a login link, don’t click on it under any circumstances. Instead, type www.slsp.sk in a new browser window and you have a guarantee that you definitely get to the right bank’s page.
What to do if the link leads to a specific subpage that is not easy to enter into the browser? For example, a “friend” sends us a link to an item from bazos.sk. In that case, after opening the link, we immediately check whether we are really on the page we are supposed to be on and not on a fake one. For example, if it’s a link to bazos.sk, after opening the URL, we check whether we are actually on the website www.bazos.sk
and not on some shady address such as bazos.my-site.com. Attackers also like to use a variety of URL shorteners like bitly.com. For such links, you need to pay attention immediately and be particularly cautious.
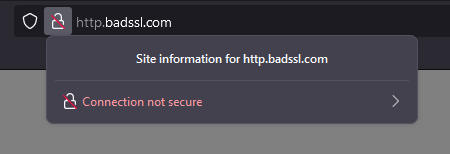
We also check if the site uses encryption and has a valid certificate. To do this, click on the lock to the left of the URL bar. See what the information about the certificate looks like on the slsp.sk website:
If the lock next to the panel is crossed out, it means that the page doesn’t use encryption at all. Don’t enter any data on this type of page. Today, encryption is standard and is used by all major trusted sites.
What if we’ve been fooled by a fraudster and entered the login details on a fake site?
In that case, action must be taken immediately. If we still have access to the account, we’ll need to change the password immediately. If the attacker has already changed our password, call support and try to explain the whole situation. If you have entered your credit card details on a fake website, you need to block your card via internet banking and report possible misuse. This prevents an uncomfortable situation when the attacker already abuses the card. Getting to the money afterwards is much more difficult.
Do you use the same password for all accounts? Mistake!
A major problem is when we use the same password for multiple services. If the phishing attack is successful and the attacker finds out our e-mail and password, the door will open not only to the given service, but also to all other services where we have the same password.
In this case, the attack may be a very serious problem. Remember the principle of using different passwords for different services. Ideally completely random or at least different password variants.
How do I know if my password has been compromised?
There is another problem related to using the same password on different websites.
If an attacker hacks the service and gets our password, they get access to all the services where we use the same password.
Fortunately, there is a website that monitors leaked passwords. There you can easily check if your e-mail address is on any of the lists. Open the URL
https://haveibeenpwned.com/
and type your e-mail address.
If our address has been positively identified in any of the leaks and we use the same password on different websites, it’s certainly advisable to change it immediately.
Two-factor authentication
Nowadays, many Internet services offer two-factor authentication. In addition to the password, we need one more extra entry to successfully log in – for example, to type in a code from a text message. We certainly recommend activating this type of login wherever possible. Even if an attacker somehow gets our password, they won’t get into the account.
Brute force attack
In addition to the above mentioned methods, one of the most common attacks on passwords is a brute force attack. In this type of attack, an attacker tries to log different combinations of passwords. It will start from 1, 2, 3, etc., through 11, 12, 13 until they get to more complicated passwords like 156113216. An attack doesn’t have to be just about numeric passwords. The same procedure can be applied to any character. Generally, the longer the password is and the more different character sets it contains, the better. A high-quality password should contain at least 12 characters, including at least one number, a lowercase letter, an uppercase letter and preferably a special character like a dot, an exclamation mark or something similar.
Dictionary attack
In addition to the brute force attack, the so-called dictionary attack is also often used. In this case, an attacker gradually tries the most commonly used words such as password, qwertz, peter, 123123, etc. The dictionary may contain nouns, most commonly used passwords, names from the calendar. In addition, this attack can be combined with brute force and each word from the dictionary is e.g. supplemented by a year, i.e. the attacker tests e.g. peter1978, peter1979, etc. Therefore, it’s very important that the password doesn’t contain commonly occurring phrases, names, years, etc.
Conclusion
In conclusion, we’ll summarize how to avoid being caught in four simple points:
- Every time we receive an e-mail with a URL, we need to be vigilant. Even if it’s an email from a bank / trusted friend / family, we must assume that it was sent by an attacker in order to retrieve our data.
- Remember the principle of using different passwords for different services.
- We recommend activating two-factor authorization wherever possible.
- A high-quality password should contain at least 12 characters, including at least one number, a lowercase letter, an uppercase letter and preferably a special character like a dot, an exclamation mark or something similar.